AI workflow platforms are revolutionizing business operations but come with heightened security risks, including data leaks, model theft, and regulatory challenges. This article reviews six top-rated AI security solutions - Prompts.ai, Check Point GenAI Security Solutions, Palo Alto Networks Prisma AIRS, Lasso Security Platform, Zscaler AI Security Controls, and SentinelOne Singularity Platform - designed to address these issues. Each platform offers unique features like real-time data protection, seamless integrations, and compliance tools to meet enterprise needs.
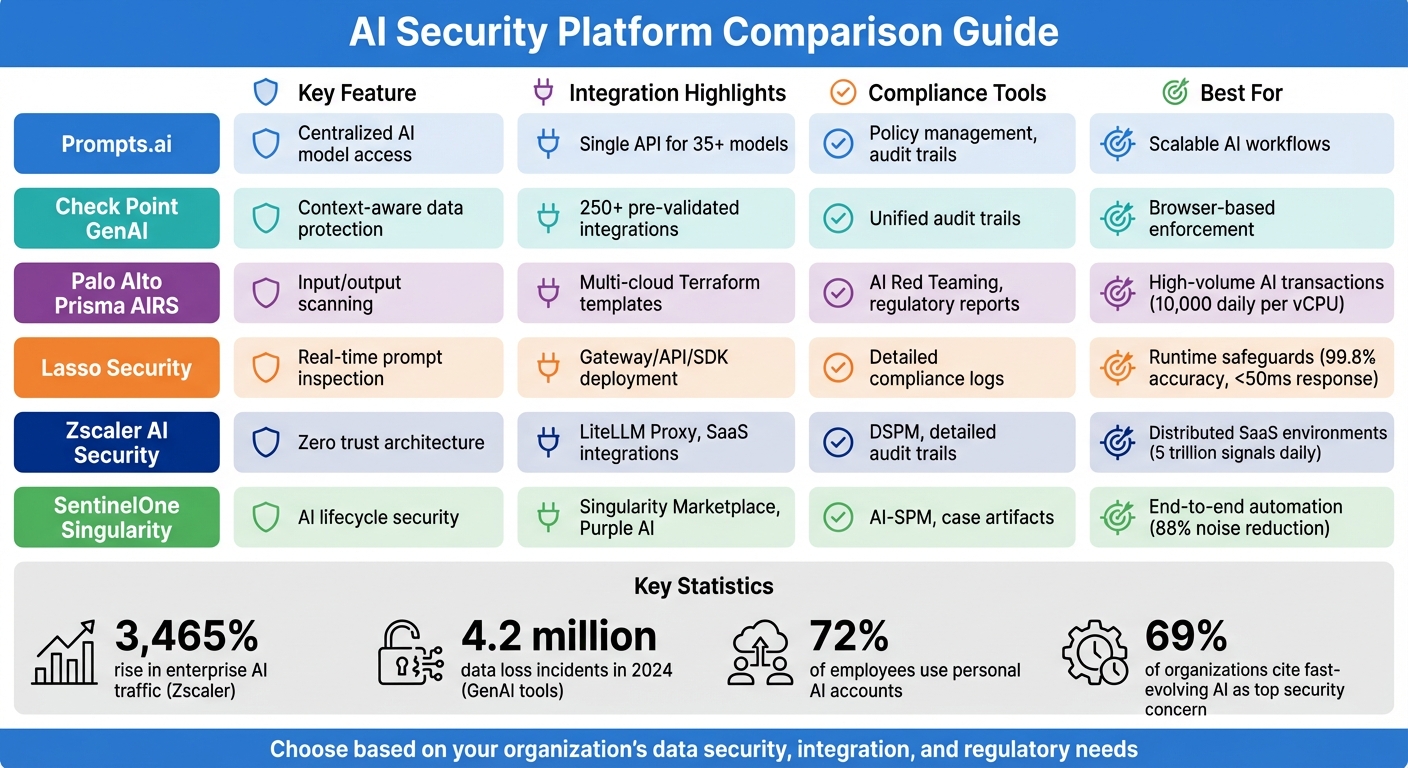
| Platform | Key Feature | Integration Highlights | Compliance Tools | Best For |
|---|---|---|---|---|
| Prompts.ai | Centralized AI model access | Single API for 35+ models | Policy management, audit trails | Scalable AI workflows |
| Check Point GenAI | Context-aware data protection | 250+ pre-validated integrations | Unified audit trails | Browser-based enforcement |
| Palo Alto Prisma AIRS | Input/output scanning | Multi-cloud Terraform templates | AI Red Teaming, regulatory reports | High-volume AI transactions |
| Lasso Security | Real-time prompt inspection | Gateway/API/SDK deployment | Detailed compliance logs | Runtime safeguards |
| Zscaler AI Security | Zero trust architecture | LiteLLM Proxy, SaaS integrations | DSPM, detailed audit trails | Distributed SaaS environments |
| SentinelOne | AI lifecycle security | Singularity Marketplace, Purple AI | AI-SPM, case artifacts | End-to-end automation |
These platforms tackle AI-specific vulnerabilities while ensuring compliance and scalability. Choose based on your organization's data security, integration, and regulatory needs.
AI Security Platform Comparison: Features, Integration & Best Use Cases
Prompts.ai brings together over 35 large language models, including GPT-5, Claude, LLaMA, and Gemini, into a single, secure platform. By centralizing AI access, it eliminates the need for multiple tools and ensures organizations can maintain strict security measures while using various models without risking sensitive data.
Prompts.ai ensures sensitive data stays secure by routing all AI interactions through a unified gateway. This centralized approach reduces the risks associated with unmonitored AI tools, providing an added layer of protection against data exposure.
Integration is simplified with Prompts.ai's single API connection, which links workflow platforms while reducing the risks and challenges of managing multiple direct integrations. The platform’s financial operations module tracks every token in real time, offering full transparency across all models. This system can quickly detect unusual activity, helping to identify potential security threats.
The platform includes robust policy management and governance tools, specifically designed for generative AI workflows. Organizations can enforce security protocols and maintain detailed audit trails for every interaction, ensuring compliance with regulatory standards. These features provide critical support during regulatory reviews and adapt effortlessly as organizational needs expand.
Prompts.ai’s pay-as-you-go TOKN credit system aligns costs with actual usage, making it easier for organizations to scale their AI workflows. Teams can add new models, users, and workflows in minutes, all while maintaining consistent security protocols without the need for complex reconfigurations. This flexibility addresses the growing demands of AI-driven operations.
Check Point's Infinity GenAI Protect identifies GenAI services, assesses their risks, and uses AI-driven data protection to prevent sensitive data leaks. Unlike traditional tools that depend on simple keyword detection, this platform employs context-aware analysis to interpret unstructured, conversational data in AI prompts. This method enhances its ability to protect data, integrate seamlessly, and support compliance efforts.
The platform detects unauthorized AI usage that conventional tools might miss. This level of visibility is especially important after incidents like the accidental exposure of 38 terabytes of private data, including passwords and internal communications, by a major AI research team due to cloud storage misconfigurations. Check Point’s browser extensions allow for quick installation and immediate policy enforcement directly within the browser.
"To understand whether content entered into a prompt is sensitive, our context-aware analysis delivers precision control" - Check Point Software
Check Point provides 14 Model Context Protocol (MCP) servers that turn APIs into natural language interfaces. Security teams can query policies in plain language using tools like Claude Desktop, eliminating the need for custom scripts. The platform integrates seamlessly with Check Point firewalls and supports over 250 pre-validated integrations with third-party solutions, including Microsoft Defender, Microsoft Entra ID, and CrowdStrike Falcon. These open-source MCP servers are available on the MCP Marketplace and can be deployed on-premises, ensuring sensitive security data stays within your infrastructure.
The platform’s unified audit trail records all risky user activities, offering detailed documentation for regulatory reviews. Security teams can ask questions like "Is my security policy compliant with PCI-DSS?" and receive structured, real-time reports. This natural language interface simplifies compliance processes and helps reduce the volume of daily alerts.
Palo Alto Networks Prisma AIRS secures AI workflows through its "scan-model-scan" methodology, which inspects inputs and verifies outputs. With the ability to handle 10,000 AI transactions daily per vCPU, it’s designed for enterprises managing high transaction volumes.
The platform’s AI Runtime Firewall prevents prompt injections and data leaks. Enterprise DLP allows organizations to define custom profiles that flag sensitive data before it leaves their systems. Additionally, the Security-as-Code feature integrates threat detection into application source code using a REST API and Python SDK, enabling developers to scan prompts programmatically during the development process.
"What makes Palo Alto Networks AI Runtime stand out are three things. It has three functionalities - built-in data security, malware security and AI security." - Sunil Agrawal, CISO, Glean
Prisma AIRS supports payloads of up to 2 MB for synchronous scans and 5 MB for asynchronous scans, with a capacity to handle up to 100 URLs per request. These safeguards apply consistently across both public and private AI models.
Prisma AIRS integrates seamlessly with Microsoft Copilot Studio via its Security Webhooks API and with TrueFoundry AI Gateway, ensuring uniform policy enforcement across hundreds of LLMs through a single integration. Automated deployments using Terraform templates for AWS, Azure, and GCP simplify maintaining consistent security across multi-cloud environments.
"Microsoft is committed to helping organizations innovate with AI in a secure and trusted way. By collaborating with Palo Alto Networks, we're strengthening agent security in Microsoft Copilot Studio, delivering real-time protection and visibility so customers can confidently bring AI into their business." - Shay Gurman, Vice President, Microsoft Copilot Studio
The platform also features a dedicated Model Context Protocol (MCP) Server, centralizing security for AI agents using this standard. Starting December 2025, autoscaling support for software firewalls will automatically adjust security infrastructure to handle peak AI traffic.
Prisma AIRS goes beyond security by helping organizations meet regulatory requirements. Its AI Red Teaming feature conducts over 500 tailored adversarial simulations to uncover vulnerabilities before production deployment. These results align with frameworks like NIST AI-RMF, the OWASP Top 10 for LLMs, and MITRE standards. Beginning in January 2026, the Executive Reporting feature will generate high-level AI security reports to aid regulatory documentation and oversight.
AI Posture Management offers insights into the AI ecosystem, identifying excessive permissions and misconfigurations. Security teams can use this information to enforce least-privilege policies before deploying AI agents. Comprehensive audit trails, combining threat logs with detailed request tracking, support compliance reviews and incident investigations effectively.
Lasso takes AI security to the next level with a real-time control plane that seamlessly integrates into generative AI (GenAI) workflows. This platform actively inspects prompts, retrieved context, and model outputs during inference, ensuring secure operations without compromising speed. With an impressive 99.8% accuracy in detecting content, context, and intent, and response times under 50ms per request, Lasso provides a cost-effective alternative to traditional security methods.
Lasso's Context-Based Access Control (CBAC) goes beyond conventional role-based systems by evaluating real-time data sensitivity, user intent, and conversation history before approving responses. This approach offers a more dynamic and precise layer of protection. Research from Lasso shows that 13% of generative AI prompts involve sensitive organizational data, underscoring the importance of runtime safeguards.
The platform automates threat remediation without disrupting workflows. Sensitive data is masked, personally identifiable information (PII) is redacted, and unauthorized tool calls are blocked on the spot. Additionally, the Shadow AI Discovery feature identifies unsanctioned GenAI tools and browser extensions, bringing them under proper governance.
"Lasso's full security suite has been crucial in fortifying our GenAI applications. Their approach ensures our organization, customers, data, and employees stay protected from various attacks while allowing me full control over my environment." - Gil Ohayon, CIO
By combining robust data protection with seamless integration, Lasso strengthens workflows while maintaining compliance and security.
Lasso offers flexible deployment options, including Gateway, API, or SDK integration, all achievable with just a single line of code. The platform supports the Model Context Protocol (MCP), which secures connections between large language models (LLMs) and external systems like Jira, Slack, GitHub, and databases. This governance extends to the protocol level, enforcing policies that prevent prompt injection and unauthorized data leaks.
Lasso also integrates across the tech stack, connecting with existing systems like SIEM, SOAR, ticketing platforms, and messaging tools. Available on AWS Marketplace since July 2024 and Microsoft Azure Marketplace since June 2025, Lasso has further enhanced its offerings through a partnership with Scytale in April 2025, automating compliance and governance for enterprises.
Every decision enforced by Lasso is logged with detailed reasoning and mapped to compliance frameworks such as the EU AI Act, GDPR, HIPAA, and SOC 2. This ensures audit-ready evidence of adherence to both internal policies and regulatory requirements. Automated enforcement ensures fine-grained control over data flows, addressing gaps often overlooked by traditional systems. For example, the platform can automatically detect and revoke access for orphaned or stale accounts, closing potential vulnerabilities in real time.
"Lasso's investigative tools have been incredibly valuable. But they also help to prevent risks proactively by educating our employees about responsible AI usage. This has been key to enabling innovation while maintaining compliance and security." - Itzik Menashe, CISO & VP IT Productivity
Designed for scalability, Lasso supports infrastructure-as-code (IaC) tools like Terraform and Pulumi, enabling security measures to grow alongside cloud and hybrid AI deployments. The platform has been rigorously tested with over 3,000 attack simulations, ensuring resilience at an enterprise scale. With projections indicating that 80% of enterprises will adopt GenAI APIs or applications by 2026, Lasso’s ability to maintain consistent security across expanding workflows is critical.
Zscaler employs a zero trust architecture to ensure strict least-privilege access for all AI-related activities. With its infrastructure processing over 5 trillion signals daily, the platform continuously adjusts security measures in real time. This approach has been vital in managing a staggering 3,465% rise in enterprise AI traffic year-over-year, enabling organizations to adopt AI rapidly while maintaining strong security protocols.
The AI Guard feature actively scans prompts and responses, blocking threats such as prompt injections, jailbreak attempts, and malicious code before they can interact with AI models. Zscaler's Data Loss Prevention (DLP) system leverages over 100 predefined dictionaries - including those for Source Code, PII, PCI, and PHI - to detect and prevent sensitive data leaks automatically. In 2024, generative AI tools like ChatGPT and Microsoft Copilot were linked to 4.2 million data loss incidents, underscoring the need for robust runtime protection.
To further secure data, Zscaler uses browser isolation, rendering AI applications as "pixels" in a virtual browser. This setup allows users to interact with AI tools while restricting clipboard use, file uploads, and downloads, minimizing data exfiltration risks. Additionally, the Shadow AI Discovery feature identifies and categorizes unsanctioned AI applications within large-scale deployments, offering organizations enhanced visibility into how AI tools are used across teams.
"We had no visibility into [ChatGPT]. Zscaler was our key solution initially to help us understand who were going to it, what were they uploading, and then providing awareness." - Jason Koler, CISO, Eaton Corporation
Zscaler integrates seamlessly with LiteLLM Proxy, enabling developers to set security guardrails directly within configuration files for real-time filtering during LLM API calls. It supports major cloud AI services such as Amazon Bedrock, Microsoft Azure Foundry AI, and Google Vertex AI, as well as unmanaged services like Hugging Face and Ollama. The Zero Trust Exchange architecture acts as an inline proxy, intercepting traffic between users, devices, and AI applications, eliminating the need for complex integrations for every new tool.
For Microsoft Copilot, Zscaler maps OneDrive data, detecting misconfigurations and anomalies to enhance security. The platform also connects with IT Service Management (ITSM) tools and Data Security Posture Management (DSPM) solutions, streamlining risk remediation processes and integrating smoothly into existing workflows.
"It's going to be critical for us as an organization to work with partners and work with technologies that are willing to incorporate AI and that are willing to bring AI in to allow us to scale up rapidly." - Jon Fowler, CISO, Consilio
These integrations provide the foundation for enforcing stringent, real-time compliance measures.
Zscaler ensures regulatory accountability by maintaining detailed AI audit trails that log user activities, prompts, responses, and application usage. Its Data Security Posture Management (DSPM) tool identifies, classifies, and protects sensitive data across cloud environments, aligning with GDPR, CCPA, and HIPAA standards. Real-time guardrails help organizations comply with frameworks like the EU AI Act and the NIST AI Risk Management Framework, ensuring security and adherence to regulatory requirements in evolving AI workflows.
The platform also automates incident management tasks, such as handling user justification requests, compliance coaching, and escalation processes. Its multimode CASB consolidates compliance visibility, enabling administrators to detect and address misconfigurations that could undermine benchmarks across web, SaaS, and endpoint environments.
Zscaler's unified cloud architecture and single-agent design allow it to scale security measures across web, email, and endpoints without additional hardware. This approach reduces opportunities for lateral movement by attackers by approximately 94%, significantly limiting the impact of compromised user accounts. With nearly 59.9% of AI/ML transactions blocked in 2024 due to security concerns, Zscaler's granular session controls - permitting prompts but restricting bulk data uploads - help maintain productivity while safeguarding data. This balance ensures operational efficiency for enterprises increasingly driven by AI workflows.
SentinelOne offers a comprehensive approach to securing the entire AI lifecycle. Recognized as a Leader in the Gartner Magic Quadrant for Endpoint Protection Platforms for five consecutive years (2021–2025), the platform also achieved 100% detection with zero delays in the 2024 MITRE Engenuity ATT&CK Enterprise Evaluation. Its AI-powered automation reduces noise by 88% compared to the industry median, enabling security teams to concentrate on real threats rather than wasting time on false positives.
The platform's Data Security Posture Management (DSPM) identifies and classifies sensitive data, such as PII, credentials, and proprietary information, within cloud-native databases before it reaches AI workflows. SentinelOne's "Safe-to-Train" gate ensures that high-risk or sensitive data is excluded from AI training processes, addressing a critical issue: once sensitive data is embedded in model weights, it becomes nearly impossible to remove. This proactive measure is crucial for organizations developing AI systems.
SentinelOne also includes a Prompt Security layer to defend against prompt injection attacks, jailbreaks, and data leaks by filtering inputs and outputs in real time. This ensures confidential information and intellectual property are not unintentionally exposed to AI models or code assistants. For runtime protection, the platform's Cloud Workload Protection (CWPP) secures AI execution environments, providing continuous monitoring and safeguarding against unauthorized access across VMs, containers, and Kubernetes clusters.
"SentinelOne was really like a self-driving car. It aided the team to do bigger and better things." - Steve O'Connor, Director of IT, Aston Martin Lagonda LTD
This robust protection creates a strong foundation for secure and seamless integrations.
The Singularity Marketplace serves as a centralized hub for third-party integrations, allowing the platform to connect with various security and workflow tools through an API-first design. Unlike closed systems, SentinelOne supports open ingestion of external telemetry, reducing integration challenges in multi-vendor environments. Scoped API keys enable federated search and workflow integrations while maintaining least-privilege access.
SentinelOne's Purple AI, an agentic AI analyst, collects data from both the Singularity platform and third-party sources to deliver comprehensive threat visibility. Organizations using Purple AI report an average of $435,000 in annual productivity gains, as the system autonomously accelerates threat hunting and investigation processes. The platform’s lightweight agent spans endpoint, cloud, and identity environments, simplifying deployment and management as AI workflows grow.
"Innovation is king and we have to move fast. SentinelOne gives us the confidence to move quickly, knowing that it has our back." - Lou Senko, Chief Availability Officer, Q2
SentinelOne's AI Security Posture Management (AI-SPM) offers a consolidated inventory of AI assets, such as training jobs, development notebooks, and inference endpoints, to detect misconfigurations and prevent over-privileged containers. Purple AI enhances compliance efforts by generating detailed case artifacts and audit trails required for regulatory reporting. The Singularity Identity feature defends against credential misuse, while Network Discovery provides instant asset inventories and flags rogue devices, supporting internal policies and regulatory tracking.
By leveraging behavioral models and machine learning instead of signature-based detection, SentinelOne can identify zero-day attacks and emerging threats that traditional compliance tools might overlook. With a 4.8/5 rating on Gartner Peer Insights and a 96% recommendation rate from verified users, the platform enables fast incident resolution while ensuring compliance with global AI regulations, including the EU AI Act.
These compliance capabilities integrate seamlessly into scalable operations.
SentinelOne's hyperautomation features include a no-code workflow builder with over 100 pre-built integrations, enabling security teams to automate triage, investigation, and response processes at scale. This addresses a critical challenge: without advanced automation, security teams are unable to investigate 43% of daily alerts. The platform's unified architecture eliminates the need for multiple agents across security surfaces, reducing complexity as AI operations expand.
With the global datasphere expected to reach 10.5 zettabytes by 2028, scalable security infrastructure is becoming increasingly important. SentinelOne’s approach allows organizations to grow their AI-driven workflows without a proportional increase in security overhead. Purple AI acts as a force multiplier, handling routine tasks so analysts can focus on strategic priorities.
"SentinelOne is our defense so that we can focus on our offense." - Brian Fulmer, Senior Director of IT, Golden State Warriors
Here’s a breakdown of the strengths and challenges associated with each solution mentioned earlier:
Check Point GenAI Security Solutions
Check Point offers browser extensions for instant policy enforcement and uses over 50 AI engines for real-time threat analysis. This makes it a strong choice for organizations needing quick and seamless security integration within their workflow platforms.
Palo Alto Networks Prisma AIRS
Palo Alto Networks provides comprehensive lifecycle security, from development to production, with specialized protections like defense against memory manipulation. Its integration works especially well for teams already utilizing the Palo Alto ecosystem.
Lasso Security Platform
Lasso Security is designed to protect large language model (LLM) interactions and is easily accessible through AWS and Azure marketplaces, simplifying procurement for cloud-based teams.
Zscaler AI Security Controls
Zscaler employs an agentless, API-native deployment model that scales effectively across distributed SaaS environments. However, organizations in regulated industries should ensure its compliance certifications align with their specific requirements.
SentinelOne Singularity Platform
SentinelOne delivers enterprise-grade security solutions but requires experienced security teams to manage its advanced AI policies effectively.
This summary highlights the trade-offs of each solution, helping organizations align their security strategies with their operational goals. The right choice will depend on factors like data protection needs, ease of integration, and compliance requirements.
One challenge for smaller teams is that most enterprise-grade solutions do not offer fixed pricing. Costs are typically influenced by variables like the number of users, integrations, and data volume, which can make budgeting more complex. Additionally, the move toward inline remediation - real-time redaction of prompts and responses - marks a significant shift in addressing the fast-evolving demands of AI-driven workflows.
Choosing the right platform involves matching your team's needs with effective safeguards and scalable operations. For small- to medium-sized teams aiming for cost-efficient protection without complex engineering, agentless solutions provide a quick and straightforward setup. This analysis highlights that both technical compatibility and predictable costs are key factors in decision-making.
For organizations in regulated fields like healthcare, finance, or insurance, it's essential to focus on vendors with SOC 2 Type II certifications and compliance frameworks for standards like HIPAA, PCI, or GDPR. Features like strong data protection, seamless integration, and compliance-ready tools are critical across all reviewed solutions. The move towards inline remediation is especially important, as it allows platforms to mask or block sensitive data before it reaches an LLM, addressing vulnerabilities instantly instead of relying solely on after-the-fact alerts.
With 72% of employees reportedly using personal AI accounts, regular audits using SSO logs or surveys are crucial. Budget predictability can be challenging since most enterprise platforms don't offer fixed pricing, and costs often depend on user count, integrations, and data usage. Deciding between a fully managed solution or one that supports internal customization will depend on your available resources.
Focus on platforms that enforce real-time security measures rather than relying on monitoring tools alone. With 69% of organizations identifying the fast-evolving AI landscape as their top security concern - surpassing even ransomware threats - your security approach must evolve as quickly as AI workflows are adopted within your teams.
Workflow platforms need to tackle major risks such as data poisoning, adversarial inputs, data leaks, identity misuse, and supply chain vulnerabilities. These risks can undermine the security and reliability of AI workflows. By focusing on these issues, platforms can better protect sensitive information, maintain system integrity, and uphold compliance standards in AI-powered operations.
Implement AI runtime security measures that intercept unsafe inputs and outputs with lightning-fast response times - under 10 milliseconds - ensuring user experience remains smooth. These measures rely on adversarially trained models to identify exploits and enforce security policies effectively. To enhance monitoring and control, integrate SDKs or API gateways that stream telemetry data and apply real-time policies. This setup allows for seamless tracking and blocking of unsafe interactions without compromising performance.
To conduct AI workflow audits, gather evidence that demonstrates adherence to regulations such as GDPR, HIPAA, and SOC 2. Essential documentation includes audit trails for data handling, details of encryption protocols, access control measures, and records of monitoring activities. Additionally, maintain thorough documentation of compliance with privacy laws, data residency requirements, and incident response protocols. These records not only provide transparency but also confirm secure data management practices while showcasing alignment with both regulatory frameworks and internal policies.


